When evaluating the VPN service, we go beyond mere observation and willingly invest in becoming paying customers. We refrain from requesting complimentary accounts. Here’s our 13 Step Review Process For VPN:
- Purchase a subscription for each VPN service.
- Install the VPN application on our laptop, compatible with either Windows 10 or Mac OS 10.13+.
- Conduct multiple speed tests using different locations via speedtest.net.
- Verify the absence of DNS, IP, and WebRTC leaks by testing both applications and browser extensions.
- Evaluate the usability and user-friendliness of the VPN app.
- Verify the accuracy of their logging policy and jurisdiction.
- Determine if the VPN service successfully unblocks and works with Netflix.
- Confirm whether they allow torrenting and P2P (peer-to-peer) file sharing.
- Test the responsiveness and effectiveness of their customer support.
- Compile a list of the main security and privacy features offered by each VPN service.
- Check compatibility with additional platforms such as TOR, game consoles, and routers.
- Compare the cost versus the value provided by each VPN service.
- Rank the VPN services accordingly on our homepage.
This is our comprehensive approach to evaluating and rigorously testing every aspect of a VPN service:
Table of Contents
13 Step Review Process For VPN
1. Same computer & network for each VPN
What does the box contain? 13-Step Review Process For VPN By Review – itis

Introducing our resilient companion, the Lenovo IdeaPad 120S-141AP, affectionately known as “Lenny”!

To ensure technical consistency, we utilize Lenny as the designated device for testing every VPN in our evaluation. In fact, we specifically acquired Lenny for this purpose.
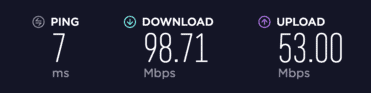
In order to maintain a standardized testing environment, we refrain from conducting VPN tests across various networks. Instead, we rely on a wired cable connection within our headquarters located in Estonia. Our network underwent multiple speed tests over several weeks to establish an average benchmark: 98 Mbps upload speed and 53 Mbps download speed.
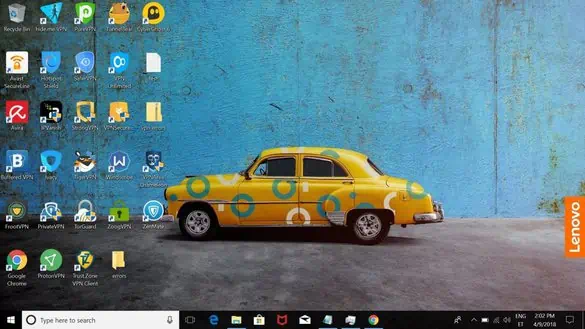
2. Bought and installed 78 VPN apps (ongoing…)
To provide you with a bit of context, allow me to offer you a sneak peek into Lenny’s desktop as it appeared a few weeks back:
Now, let’s take a moment to emphasize and ensure that this point is unmissable by utilizing bold type:
We want to make it explicitly clear that we absolutely do not accept any form of payment, bribes, favors, in-kind donations, exotic pets, cryptocurrencies, homecooked meals, or ANY kind of compensation in exchange for writing or editing a review. This principle holds true, without exception.
In fact, we personally cover the costs of every VPN service we try, ensuring complete honesty and maintaining our role as genuine consumers. We believe in unbiased evaluations without any external influences.
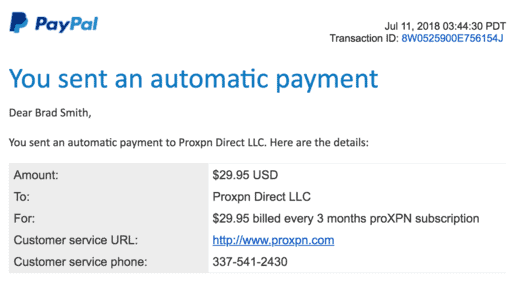
All the data we gather is obtained firsthand, distinguishing us from other reviewers who often rely on plagiarized information from other websites or fabricate data altogether. Regrettably, such practices are regrettably prevalent, but we strive to maintain the integrity of our evaluations by providing genuine and authentic findings.
3. Read through their logging policy
Have you ever taken the time to thoroughly read a logging or privacy policy? Well, we certainly have. In fact, we’ve delved into these policies over 40 times, enduring eye strain and headaches as we meticulously examined every detail.
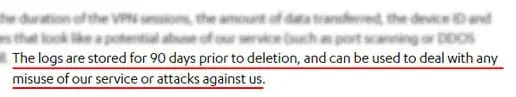
While it may not be the most enjoyable aspect of our reviews, it is undoubtedly the most crucial one. Shady companies often employ cunning language to obscure the fact that they monitor and distribute your online activities.
We painstakingly dissect the fine print to ensure that you are not being exploited or deceived in any way. Safeguarding your interests is our top priority.
4. Check their jurisdiction and history
Background and Company Information: When evaluating VPN services, we prioritize understanding the background and company details. We investigate who operates the company and their origin. Additionally, we thoroughly investigate whether the company has a history of violating user privacy or experiencing leaks. Our dedicated team collects as much information as possible on these aspects and brings it to you, ensuring transparency and empowering you to make informed decisions.
Jurisdiction: The jurisdiction in which a VPN is based holds significant importance, as it can impact the extent to which a VPN might be compelled to surrender user data to authorities when subjected to pressure. We recognize the crucial role played by jurisdiction and its implications for user privacy. To provide you with comprehensive insights, we explore the jurisdictional aspects of each VPN service, shedding light on their potential implications and ensuring you have a clear understanding of this critical factor.

5. Run multiple speed tests
No matter how secure your VPN may be, its effectiveness diminishes when downloading an episode of “Stranger Things” takes three hours. To address potential variations in service, we employ speedtest.net to conduct multiple tests on both Upload and Download speeds.
Additionally, we periodically revisit these speed tests approximately once a year to assess any alterations that might have occurred.
Regrettably, certain VPNs proved to be exceptionally sluggish in our evaluations.

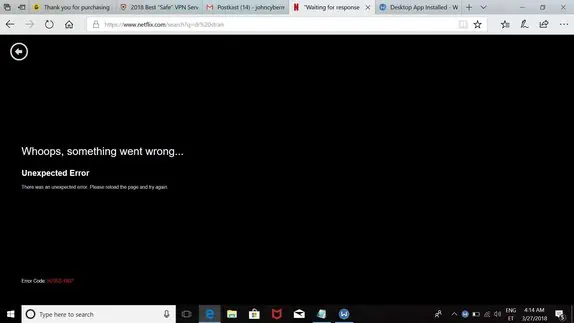
6. Tested Netflix streaming across 3 to 6 servers
Interested in a Netflix and chill session? Well, that’s only possible if it actually works. That’s precisely why we don’t rely on a single test; instead, we diligently identify the servers (if any) that are compatible with Netflix and inform you accordingly. This approach saves you both time and the frustration of dealing with potential roadblocks.
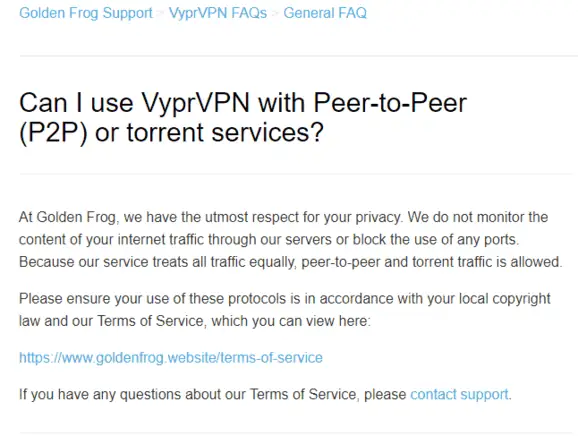
7. Read through their torrenting/P2P policy
Certain VPNs impose restrictions on P2P and torrenting activities, while others openly support and promote them. Meanwhile, some VPNs employ subtle tactics to address the matter. Our objective is to uncover the truth behind these claims, ensuring that you have the freedom to engage in the activities you desire with the VPN of your choice.
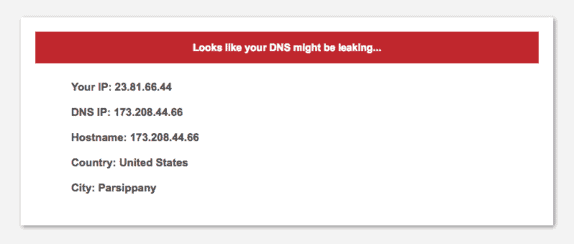
8. Test for DNS, IPv4, IPv6, and WebRTC leaks
TL; DR: IP leaks occur when your VPN fails to conceal your true IP address while you’re browsing. For instance, if you attempt to access a geo-restricted show on Netflix but encounter a block, it’s possible that your actual IP address has been revealed.
To evaluate the effectiveness of a VPN, we conduct targeted tests on typical vulnerabilities to assess its performance.
9. Graded their usability & user-friendliness
Even the most secure VPN in existence loses its value if it requires an advanced degree in Computer Sciences to navigate. We assess factors such as setup time, user-friendly interfaces, and configuration simplicity to gauge the VPN’s accessibility for the average user.
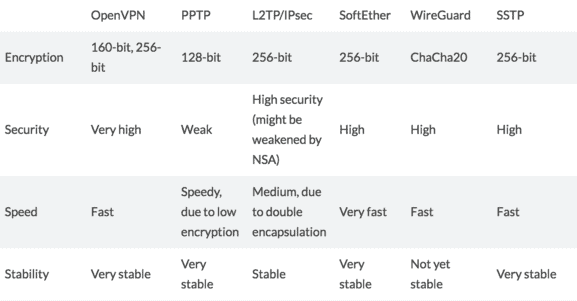
10. Evaluate each VPN security and privacy features
Various VPN services cater to specific use cases, such as business or personal needs, while certain “premium” features should ideally be included as standard across all VPNs. We assess and evaluate…
- Available security protocols
- Types of encryption
- Instant disconnect feature (kill-switch) in case of security loss
- Maximum number of connections allowed simultaneously (number of devices)
- Supported browser
- Quantity and geographical distribution of servers
We also examine any distinctive features that the VPN service offers, shedding light on the positive aspects as well as any drawbacks or limitations.
11. Put their customer support to the ultimate (and real!) test
It is advisable to exercise caution when a company claims to provide “best in class” customer service. To evaluate the responsiveness and competency of the support team in addressing common VPN issues, we proactively engage with them through various channels such as support tickets, phone calls, and chat interactions.
12. Test compatibility with routers, TVs, TOR, and consoles
What’s the use of a VPN service if it’s not compatible with your devices? We conduct thorough tests on various setups to ensure compatibility, saving you from investing in a solution that won’t work with your gadgets.
Additionally, we evaluate whether the VPN service can be used in conjunction with TOR to provide an extra layer of security. This aspect is particularly crucial for power users and individuals in sensitive environments or locations.
13. Compare the cost vs value
Indeed, pricing is a significant factor to consider. However, we evaluate it towards the end of our assessment because it makes little sense to prioritize a free product that compromises your privacy or an expensive product that fails to offer any superior features compared to more affordable alternatives.

You can take it from here…
It’s quite an extensive process, isn’t it?
With the task of reviewing those 13 points for over 70 VPN providers and ensuring our reviews stay up-to-date, it’s understandable why it takes some time to publish new reviews.
We genuinely hope that you value the thoroughness and transparency invested in our work here, and that the information we provide proves helpful in your decision-making process.
For More amazing articles related to VPN, Check out our website Over Here
To Read more similar articles, click here
Thanks for visiting our Website. If you appreciate our work, kindly show us some support in our comments section 🙂