Computer networks play an indispensable role in our modern interconnected world. From the vast internet that seamlessly connects countless devices worldwide to the local area networks (LANs) in our homes and offices, grasping the fundamentals of networking is essential for individuals and organizations alike. In this era of digital communication and information exchange, the ability to comprehend and navigate computer networks empowers us to unlock the boundless potential of technology.
The Significance of Computer Networks, Computer networks serve as the foundation of communication and data transfer in today’s society. They enable us to effortlessly share information, access valuable resources, and collaborate seamlessly with others. Whether it’s sending emails, browsing the internet, streaming videos, or utilizing cloud services, all these activities are made possible through computer networks.
Moreover, networks facilitate efficient and cost-effective sharing of resources like printers, storage devices, and internet connectivity. By understanding the fundamentals of computer networks, individuals gain the knowledge needed to troubleshoot basic connectivity issues, secure their devices and data, and make well-informed decisions regarding network infrastructure.
The Essentiality of Understanding Networking In a world where technology has become an integral part of our personal and professional lives, possessing a foundational understanding of networking is more critical than ever before. From individuals relying on networks for everyday tasks to businesses depending on networks for their operations, the ability to comprehend networking concepts ensures smoother and more efficient communication, collaboration, and productivity. Understanding networking also empowers individuals to adapt to new technologies and stay up to date with the latest trends, a crucial skill in an ever-evolving digital landscape.
Additionally, with the increasing prevalence of remote work and cloud-based services, a solid understanding of networking enables individuals and organizations to optimize their network configurations, effectively troubleshoot issues, and implement robust security measures to safeguard sensitive information.
Table of Contents
Introduction to Networking
A computer network encompasses a myriad of interconnected devices, including computers, servers, printers, and routers, all working together harmoniously to facilitate communication and resource sharing. It lies at the heart of efficient data exchange, enabling individuals and organizations to collaborate seamlessly, access shared resources, and communicate effectively. Grasping the definition and concept of computer networks is pivotal in understanding the foundational principles of networking.
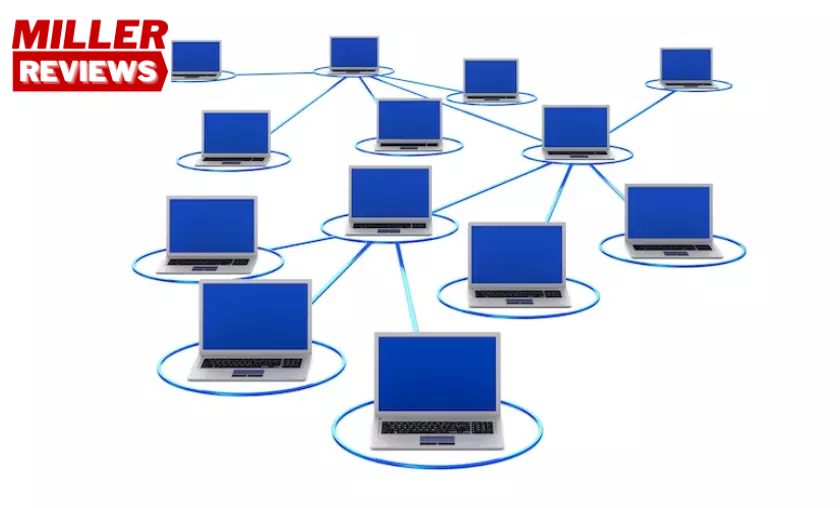
The essence of a computer network revolves around the concept of connecting devices to enable smooth communication and resource sharing. Networks are built upon a framework of protocols and technologies that govern the transmission and reception of data. By establishing these connections between devices, networks pave the way for the seamless transfer of information and foster the exchange of services like file sharing, email, and web browsing. This interconnectedness serves to enhance productivity, efficiency, and collaboration across various domains, be it education, business, entertainment, or research.
Elements Of A Computer Network
Computer networks comprise a harmonious ensemble of crucial components that collaborate seamlessly to facilitate communication and the sharing of resources. These essential elements include:
- Devices: These remarkable endpoints or nodes within a network encompass an array of interconnected entities, including computers, laptops, servers, printers, and smartphones. Their harmonious integration fosters an environment where data exchange flourishes.
- Links: The backbone of communication channels, aptly known as links, serves as the physical or wireless connections that facilitate the seamless transmission of data between devices. These connections can manifest as wired marvels, such as Ethernet cables, or as the magic of wireless technology, exemplified by the likes of Wi-Fi.
- Protocols: The unsung heroes of network operation, protocols stand as a definitive set of rules and standards that govern the intricate dance of data transmission, reception, and processing within a network. Remarkable examples of network protocols include the ubiquitous IP (Internet Protocol), the ever-reliable TCP (Transmission Control Protocol), and the indomitable HTTP (Hypertext Transfer Protocol).
- Network Interface: Acting as the gateway to connectivity, the network interface represents the remarkable fusion of hardware and software components that enable devices to elegantly embrace the network. From the sturdy network card gracing a computer to the nimble Wi-Fi adapter adorning a smartphone, these interfaces embody the gateway to limitless connectivity.
Types Of Computer Networks
Computer networks gracefully unfold into distinct categories, delineated by their scale, geographical coverage, and purpose. Let’s explore some of the common types that epitomize the realm of computer networks:
- Local Area Network (LAN): LANs, covering limited geographical areas like homes, offices, or schools, facilitate seamless communication and resource sharing among devices in the same vicinity.
- Wide Area Network (WAN): WANs extend their reach across larger geographical areas, connecting multiple LANs or even global networks like the Internet. They employ various communication technologies to bridge long distances.
- Metropolitan Area Network (MAN): MANs serve cities or metropolitan areas, interconnecting multiple LANs within a defined geographic region.
- Wireless Networks: These networks rely on wireless communication technologies, such as Wi-Fi or cellular networks, enabling device connectivity without the need for physical cables.
Understanding the elements and types of computer networks provides a foundation for comprehending how different networks are structured, connected, and utilized to meet specific communication and resource-sharing needs.
Networking Fundamentals
Communication Protocols
The Backbone of Networks Communication protocols serve as the indomitable backbone of computer networks, shaping the rules and procedures for flawless data transmission and exchange. They lay the foundation for devices within a network to decipher and interpret the flowing information. These protocols establish guidelines for data formatting, addressing, and verification, ensuring utmost accuracy.

The networking realm thrives on common protocols like the Internet Protocol (IP), Transmission Control Protocol (TCP), User Datagram Protocol (UDP), and Ethernet. Each protocol assumes a specific role in fostering different facets of network communication, be it routing, error correction, or reliable data delivery. A profound understanding of communication protocols is paramount to comprehending device communication, ensuring seamless compatibility between network devices, and skillfully troubleshooting network issues.
IP Addresses & Subnetting
Identifying Devices on a Network IP addresses, those unique numerical identifiers bestowed upon devices connected to a network, act as the guiding light to locate and identify each entity within the intricate web. These addresses, embracing the realms of IPv4 (32-bit) or IPv6 (128-bit), gracefully present themselves in the familiar dotted-decimal format (e.g., 192.168.0.1).

The art of subnetting, in turn, dances to the rhythm of dividing a network into smaller subnets, fueling the efficient utilization of IP addresses and empowering network administrators to expertly manage resources. Subnetting breathes life into the creation of subnets by allocating portions of the IP address space to each unique subnet. A profound grasp of IP addresses and subnetting holds the key to network configuration, device addressing, seamless connectivity, and the optimization of network performance.
Network Topologies
How Devices are Connected Network topologies define how devices are interconnected within a network. They determine the physical or logical structure of the network and the paths through which data travels. Common network topologies include bus, star, ring, mesh, and hybrid topologies. In a bus topology, devices are connected to a central cable or bus. In a star topology, devices are connected to a central hub or switch. In a ring topology, devices are connected in a closed loop, where data flows in one direction.
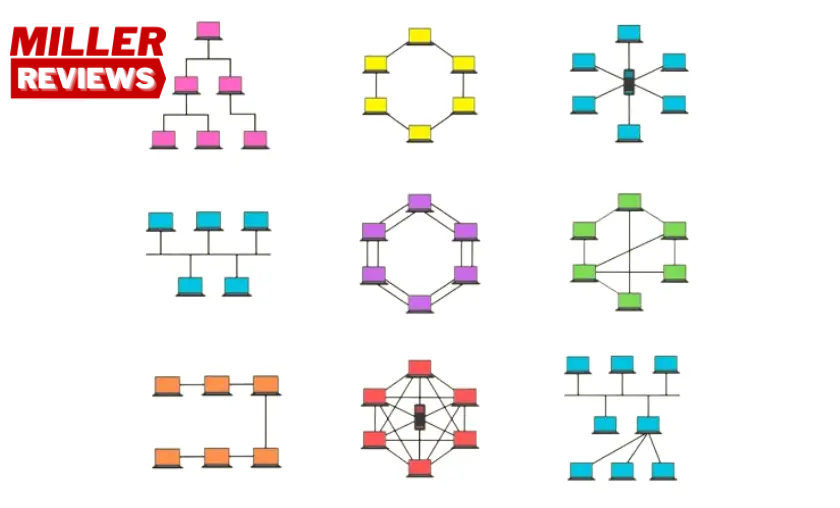
In a mesh topology, devices are interconnected with multiple redundant paths. Hybrid topologies combine elements of different topologies. Understanding network topologies is crucial for network design, determining how devices communicate and share data, and ensuring reliable and efficient network connectivity.
Mastering the fundamentals of communication protocols, IP addresses, subnetting, and network topologies forms the bedrock of understanding the essence of computer networks. These concepts, interwoven into the fabric of network infrastructure, pave the way for seamless communication, device identification, and the artistry of efficient data transfer. By embracing these networking fundamentals, individuals are bestowed with the wisdom to configure networks, troubleshoot connectivity hiccups, and craft robust and effective network architectures.
Local Area Networks (LANs):
Understanding LANs & Their Purpose
In the captivating realm of networking, a Local Area Network (LAN) emerges as a transformative force, adorning small geographic areas like homes, office buildings, or school campuses. LANs, crafted with precision, serve as the conduits that foster impeccable communication and seamless resource sharing among devices within their intimate domains.

At the core of their existence lies the noble purpose of enabling efficient and reliable data transmission, facilitating collaboration, and granting access to shared resources. Like pillars of connectivity, LANs lay the foundation for local communication, effortlessly bridging devices such as computers, printers, servers, and other marvels of network-enabled technology, allowing them to harmonize and interact flawlessly. Within the sanctuary of a specific location, LANs play a pivotal role in orchestrating a symphony of tasks, ranging from file sharing and printer sharing to local data backup and inter-device communication.
Ethernet & Wi-Fi
The grand tapestry of LANs unfolds, showcasing two illustrious technologies that grace their realm: Ethernet and Wi-Fi. Ethernet, an embodiment of wired networking prowess, manifests through the graceful dance of Ethernet cables, weaving physical connections that unite devices. With its hallmark of high-speed and unwavering data transmission, Ethernet emerges as the choice of discerning souls who crave stable and swift network connections.

Devices such as desktop computers, servers, and network printers revel in the embrace of Ethernet’s reliability. Wi-Fi, on the other hand, emerges as a wireless marvel, breathing life into the concept of freedom and connectivity without the shackles of physical cables. Through the ethereal realm of radio waves, Wi-Fi enables devices like laptops, smartphones, tablets, and the ever-advancing Internet of Things (IoT) wonders to join the LAN’s embrace. Within the LAN’s coverage area, Wi-Fi offers a harmonious marriage of flexibility and mobility, catering to the needs of wireless connectivity seekers.
LAN Components
The intricate tapestry of LANs unfurls, unveiling the key components that intertwine to shape network connectivity and communication. Enter the captivating realm of switches, routers, and access points. Switches, bearing the torch of connectivity, stand tall as devices that bind multiple entities within a LAN, allowing them to converse and collaborate effortlessly. Like wise gatekeepers, they channel data packets to their intended recipients, guided by the sacred MAC addresses, reducing congestion and amplifying network efficiency. Routers, the illustrious architects of connectivity, don the mantle of linking diverse networks together, ushering a LAN to the grand stages of the internet.

Their wisdom determines the most optimal paths for data packets to embark upon, seamlessly traversing different networks to reach their cherished destinations. And let us not forget the radiant presence of access points (APs), the ethereal bridges between wired and wireless realms. These enchanted devices bestow the gift of Wi-Fi connectivity upon wireless devices, expanding the LAN’s reach and granting wireless communication powers to devices within its loving embrace. Access points stand as beacons of connection, pivotal in establishing wireless harmony and extending the LAN’s magnificence.
Wide Area Networks (WANs)
Introduction to WANs & their Role
In the captivating realm of computer networks, a Wide Area Network (WAN) unveils its majestic presence—a marvel that extends its reach across vast geographic expanses, uniting multiple Local Area Networks (LANs) and other networks in its embrace. WANs, crafted with finesse, unfurl their purpose as catalysts for long-distance communication, empowering the seamless transmission of data and connectivity between dispersed locations.

Their noble role revolves around weaving a tapestry of reliable and secure interconnectivity between LANs or networks, bestowing upon organizations the power of unbounded communication, harmonious data sharing, and resource access across diverse locations. In the tapestry of WAN wonders, remote collaboration thrives, branch offices connect, and centralized resources become accessible. WANs serve as conduits that empower businesses and individuals to traverse the globe, surmounting physical boundaries and fostering the efficient exchange of data.
The Internet: A Global Wide Area Network
Among the grand tapestries of Wide Area Networks, one particular luminary stands tall—the Internet. A symphony of interconnected networks and devices, the Internet reveals itself as a global WAN that transcends boundaries and unites countless entities worldwide. It emerges as a boundless interconnected infrastructure that unlocks the power of global communication, information exchange, and access to a vast array of resources.

Through the Internet’s ethereal embrace, users embark on virtual voyages, connecting to websites, sending emails, sharing files, engaging in online transactions, and embracing a myriad of online services. As the crown jewel of WANs, the Internet leverages an array of technologies, from fiber-optic cables to satellite links and wireless connections, to create a ubiquitous and seamless network that empowers individuals, businesses, and organizations around the globe.
Connecting LANs with WAN Technologies
The delicate dance of connectivity between LANs across various locations, or the endeavor of merging a LAN with a WAN, often calls upon the enchanting wonders of WAN technologies. These technologies act as gateways to establish steadfast and secure connections over vast distances. Journeying through this realm, we encounter esteemed WAN technologies that breathe life into seamless connectivity. Leased lines step forward, offering dedicated point-to-point connections that ensure unwavering bandwidth and minimal latency, an ideal choice for steadfast communication.
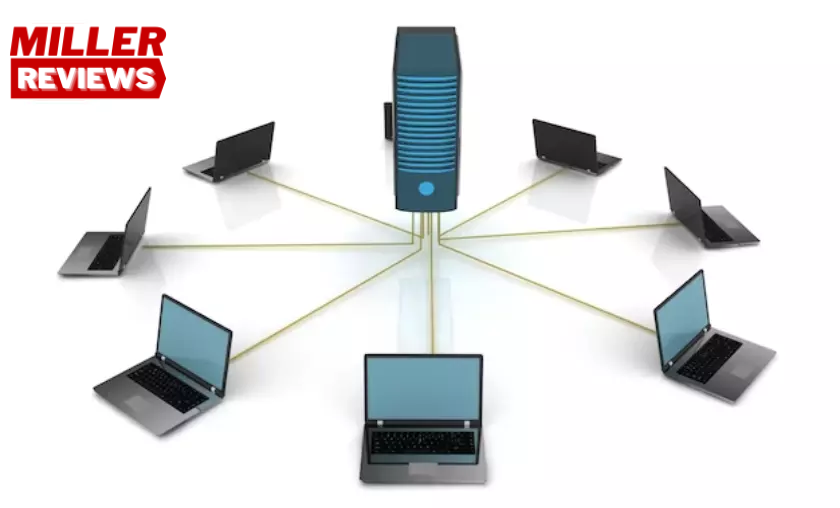
Multi-Protocol Label Switching (MPLS) emerges as a cherished technique employed by service providers, forging virtual private networks atop their network infrastructure. VPNs (Virtual Private Networks) extend their embrace, crafting secure encrypted tunnels that traverse public networks, such as the Internet, empowering protected communication between LANs or remote users. As the symphony continues, broadband internet connections, including DSL, cable, and fiber-optic marvels, grace the stage, connecting LANs to the expansive realm of WANs, offering cost-effective avenues for connectivity.
Network Devices & Equipment
Routers
The Traffic Directors of Networks: Routers, the indispensable network devices, hold the utmost significance in steering and orchestrating network traffic. Positioned at the network layer (Layer 3) of the OSI model, routers bear the responsibility of deftly navigating data packets amidst various networks. Meticulously scrutinizing destination IP addresses, routers expertly discern the optimal path for data transmission, ensuring prompt delivery to their intended recipients.

Armed with routing tables, these masters of connectivity store crucial information about network topology and available pathways. Furthermore, routers offer invaluable functionalities like network address translation (NAT), enabling multiple devices within a local network to harmoniously share a solitary public IP address. By interconnecting LANs, bridging networks to the vast expanse of the Internet, and fostering seamless communication between disparate networks, routers stand as the bedrock of network infrastructure.
Switches
Connecting Devices within a Network: Switches, the vital network devices, diligently operate at the data link layer (Layer 2) of the OSI model. Their primary function is to establish seamless connections among devices within a localized network, including computers, printers, and servers. By deftly forwarding data packets to their designated devices based on unique Media Access Control (MAC) addresses, switches foster efficient and effective communication.

In fact, switches pave the way for dedicated communication paths, ensuring optimal bandwidth allocation to each connected device, thereby enhancing network performance in comparison to shared networks. The realm of managed switches expands further, offering a plethora of advanced features such as virtual LAN (VLAN) support, quality of service (QoS) prioritization, and network monitoring capabilities. As the foundational building blocks of local area networks (LANs), switches play a pivotal role in facilitating seamless and reliable communication among interconnected devices within a network.
Firewalls
Protecting Networks from External Threats: Firewalls, the stalwart guardians of network security, stand as robust security devices, staunchly defending networks against unwarranted access, malicious intrusions, and external threats. Positioned at either the network layer or the application layer (Layer 3 or Layer 7) of the OSI model, firewalls erect an impenetrable barrier between a network and the vast expanse of external networks or the Internet. With a keen eye for detail, firewalls diligently scrutinize network traffic, meticulously filtering and monitoring data packets based on pre-established security rules and policies.

Acting as the sentinels of network defense, they possess the power to thwart suspicious or unauthorized traffic, thwart unauthorized access attempts, and identify and neutralize network attacks. Embodying an indispensable layer of protection, firewalls shield networks, ensuring unwavering network security while fortifying the sanctity of sensitive data and invaluable resources against unauthorized access and pernicious activities.
Modems
Connecting to the Internet: Modems, the ingenious modulator-demodulator devices, serve as the gateways that seamlessly link devices to the vast realm of the Internet. Their primary function involves the conversion of digital signals emanating from computers or networks into analog signals that are well-suited for transmission across telephone lines, cable lines, or other communication mediums. Operating at the foundational physical layer (Layer 1) of the OSI model, modems establish vital connections with Internet Service Providers (ISPs), enabling unfettered access to the Internet.

With remarkable finesse, modems deftly modulate digital data into analog signals for transmission, and upon receiving analog signals, they skillfully demodulate them back into comprehensible digital data for the connected device. The versatility of modems shines through as they seamlessly integrate with various communication technologies such as dial-up, DSL (Digital Subscriber Line), cable, or fiber-optic connections, seamlessly adapting to the available infrastructure and the offerings of the ISP.
Network Addressing & Naming
MAC Addresses

Unique Identifiers for Network Interfaces: MAC (Media Access Control) addresses serve as the distinctive identifiers bestowed upon network interface cards (NICs) or network adapters. These addresses, assigned by manufacturers and ingrained in the hardware itself, consist of six sets of hexadecimal digits, separated by colons or hyphens (e.g., 00:1A:2B:3C:4D:5E). Embodying permanence and global uniqueness, MAC addresses play a pivotal role at the data link layer (Layer 2) of the OSI model, guaranteeing precise delivery of data within a local network. By facilitating device identification and addressing within the same network segment, MAC addresses form the bedrock of local communication.
Domain Name System (DNS)
Mapping Names to IP Addresses: The Domain Name System (DNS) stands tall as a hierarchical naming system that flawlessly translates human-readable domain names (e.g., www.example.com) into IP addresses (e.g., 192.0.2.1) that serve as identifiers for computers and networks. Operating as a distributed database, DNS meticulously stores mappings between domain names and corresponding IP addresses. Whenever a user enters a domain name in a web browser or seeks access to a network resource, DNS takes center stage, deftly resolving the domain name to the precise IP address required.

This ingenious mechanism empowers users to effortlessly employ easily remembered domain names, freeing them from the burden of recalling and inputting complex IP addresses. With its unwavering commitment to simplifying network communication and fostering internet services, DNS emerges as a vital facilitator, seamlessly translating meaningful domain names into their corresponding IP addresses.
Dynamic Host Configuration Protocol (DHCP)
Automatic IP Address Assignment: The Dynamic Host Configuration Protocol (DHCP) proudly assumes its place as a network protocol that bestows automatic IP addresses and other network configuration parameters upon devices within a network. Simplifying the intricate process of IP address assignment, DHCP dynamically allocates and manages IP addresses from a designated pool of available addresses. Whenever a device connects to the network, it can gracefully request an IP address from a DHCP server, which in turn designates a unique IP address to that device for a predefined duration.

Alongside IP address allocation, DHCP extends its prowess to provide supplementary configuration parameters like subnet masks, default gateways, and DNS server information. By obviating the need for manual IP address configuration, DHCP offers a streamlined approach to network management and scalability, particularly in expansive environments. With its efficient and automated IP address allocation, DHCP significantly mitigates the risk of address conflicts while simplifying the intricate realm of network administration.
Network Security
Network Threats & Vulnerabilities
Safeguarding the intricate fabric of computer networks entails fortifying them against a multitude of threats and vulnerabilities that pose a risk to the confidentiality, integrity, and availability of network resources. Among the common adversaries lie the likes of malware—viruses, worms, and ransomware—alongside unauthorized access, data breaches, network attacks, and social engineering ploys, including phishing and spear-phishing.

Networks are also susceptible to vulnerabilities stemming from misconfigurations, feeble passwords, outdated software, and the absence of security patches. A comprehensive understanding of these threats and vulnerabilities forms the bedrock for implementing robust security measures that shield network infrastructure and precious data.
Authentication & Access Control
Within the realm of network security, authentication and access control assume vital roles. Authentication stands as the stalwart guardian, ensuring that users or devices are verifiably who they claim to be before granting access to network resources. Be it passwords, biometrics like fingerprint or facial recognition, smart cards, or the implementation of two-factor authentication, authentication methods play a pivotal role in verifying identities.

Complementing this, access control emerges as the gatekeeper, determining the level of access and permissions bestowed upon users or devices based on their identities and roles. Access control mechanisms, ranging from user accounts to access control lists (ACLs) and role-based access control (RBAC), become the enforcers of security policies, deftly curtailing unauthorized access to sensitive data and invaluable resources. By embracing robust authentication and access control measures, networks fortify themselves against the perils of unauthorized access and fortify their defenses against data breaches.
Encryption & Virtual Private Networks (VPNs)
Encryption, an age-old technique, assumes a pivotal role in safeguarding data traversing networks. Through the use of cryptographic algorithms, encryption transmutes plain text into ciphertext, rendering it indecipherable to prying eyes. By preserving the confidentiality and integrity of data, encryption foils unauthorized interception and tampering attempts.

Capitalizing on encryption, Virtual Private Networks (VPNs) orchestrate the creation of secure, private communication channels across public networks, such as the Internet. VPNs furnish users with the ability to establish encrypted connections to private networks, facilitating secure remote access, data transfers, and communication. By fashioning a secure tunnel for transmitting sensitive data between remote users and private networks, VPNs mitigate the risks of eavesdropping and unauthorized access, fostering an impenetrable shield of protection.
Network Services and Protocols
File Transfer Protocol (FTP)
Sharing Files Seamlessly: Enter File Transfer Protocol (FTP), a network protocol that empowers the smooth transfer of files between computers across networks, including the vast landscape of the Internet. With FTP as their trusted ally, users unlock a simple and reliable means of exchanging files between clients and servers. Seamlessly, they can upload files from their local systems to remote servers or download files from remote servers to their local machines.

Operating under the client-server model, FTP springs into action as a client initiates a connection to a server, employing FTP commands as their arsenal. To ensure an efficient transfer of commands and data, FTP ingeniously utilizes distinct control and data channels. By offering support for various authentication methods, FTP effortlessly grants users access to files based on their authorized credentials. Website maintenance, software distribution, and general file sharing endeavors find solace in the embrace of FTP’s versatile capabilities.
Simple Mail Transfer Protocol (SMTP)
Paving the Way for Email Communication: Step onto the stage, Simple Mail Transfer Protocol (SMTP), a network protocol meticulously crafted to facilitate the exchange of email messages between mail servers. As the curtain rises, SMTP adroitly takes the reins, overseeing the transmission of emails over the vast expanse of the Internet, ensuring steadfast delivery from the sender’s mail server to the recipient’s mail server. The symphony of email communication unfolds as an email is submitted to the sender’s mail server, which, in turn, enlists the prowess of SMTP to relay the message to the recipient’s mail server.

Armed with a well-defined repertoire of commands and responses, SMTP orchestrates the harmonious communication between mail servers, deftly handling the transfer and management of email messages. Validation of recipient addresses, the management of email queues, and the impeccable delivery of messages to their intended recipients all fall within the purview of SMTP’s watchful eye. To further enhance the email experience, SMTP gracefully intertwines with complementary protocols like POP3 (Post Office Protocol version 3) or IMAP (Internet Message Access Protocol), enabling users to retrieve emails from their mail servers.
Hypertext Transfer Protocol (HTTP)
Navigating the Vast Web: Prepare for a journey through the vast realms of the World Wide Web, guided by none other than Hypertext Transfer Protocol (HTTP). As the gateway to web browsing, HTTP assumes the pivotal role of enabling users to access and retrieve resources on the web. It acts as the eloquent communicator, forging a seamless connection between web browsers (clients) and web servers, ushering users into a world where web pages, files, and web-based applications come alive.

A user’s expedition commences as they enter a Uniform Resource Locator (URL) into their web browser, triggering the browser to initiate an HTTP request to the corresponding web server. In response, the server gracefully unveils an HTTP response, bearing the fruits of the user’s request—whether it be an HTML page, an image, or a file.
United under the client-server model, HTTP thrives on the artistry of bidirectional communication, as clients submit requests and servers gracefully furnish them with the sought-after resources. As a stateless protocol, HTTP encapsulates the essence of each request-response cycle, delicately preserving its independence from previous interactions. Yet, the symphony of HTTP reaches new heights as cookies and session management techniques take the stage, meticulously weaving a tapestry of stateful interactions between clients and servers.
Network Management and Troubleshooting
Monitoring & Maintaining a Network
The meticulous monitoring and maintenance of a network lie at the heart of ensuring its optimal performance, unwavering reliability, and fortified security. Embarking upon this endeavor, network management unfurls its canvas, encompassing vital tasks like device monitoring, traffic tracking, configuration management, and the fortification of security measures.

By harnessing the power of network monitoring tools, administrators wield a keen eye, enabling them to vigilantly monitor network health, detect nascent issues or bottlenecks, and take proactive strides to avert network disruptions.
The journey of network maintenance is punctuated by regular rituals, including the updating of firmware and software, the application of security patches, the fine-tuning of network configurations, and the meticulous orchestration of backups. Embracing these effective network management practices serves as a steadfast sentinel, safeguarding the seamless operation of networks, minimizing downtime, and propelling network performance to unprecedented heights.
Common Network Issues & Troubleshooting Tips
Within the intricate tapestry of networks, challenges often arise, poised to disrupt communication and tarnish the user experience. Connectivity conundrums, sluggish network speeds, DNS resolution fiascoes, and intermittent network outages are but a few of the common network tribulations that demand resolution.

Thus, the valiant troubleshooter takes center stage, wielding systematic steps to unearth and vanquish the underlying problems. This captivating quest may encompass physical connection verifications, meticulous IP configuration examinations, rigorous network connectivity testing, the meticulous scrutiny of network logs, and the relentless pursuit of faulty devices or components.
In this expedition, troubleshooters seek solace in the collaborative embrace of network administrators, Internet service providers (ISPs), and vendors, as they band together to conquer complex issues. By adhering to the tenets of troubleshooting excellence, such as commencing with simple solutions and gradually narrowing down possibilities, network maladies yield, paving the way for seamless network operation and unparalleled tranquility.
Network Performance Optimization
The art of network performance optimization serves as the catalyst for elevating efficiency, amplifying throughput, and summoning lightning-fast response times. This captivating journey delves deep into the intricate tapestry of the network infrastructure, unraveling its innermost secrets to unlock its untapped potential. Network bandwidth, traffic management, network protocols, and hardware configurations fall under the scrutinizing gaze of this process.

Embodied within this quest are the techniques of the trade, including the implementation of Quality of Service (QoS) mechanisms, which deftly prioritize critical traffic, and the adept utilization of traffic shaping, enabling the masterful control of bandwidth consumption.
Further weapons in the arsenal of optimization include the application of caching and compression techniques, artfully reducing data transfer sizes, and the meticulous optimization of network routing. Mighty network performance monitoring tools offer invaluable insights into the very heart of performance bottlenecks, empowering administrators to embark on proactive journeys to enhance network performance. With the hallowed ground of network performance fully optimized, organizations unlock a gateway to swifter, more reliable network communication, fanning the flames of enhanced productivity and unwavering user satisfaction.
Conclusion
what we’ve covered in this networking introduction. We’ve learned about the definition and concept of computer networks, explored communication protocols, IP addressing, subnetting, and network topologies. We’ve also discussed LANs, WANs, network devices, addressing and naming, network security, services, protocols, and management. Networking is incredibly important in our interconnected world, providing seamless communication, access to information, efficient data transfer, and supporting various applications. It’s essential for personal and professional growth in our digital age.
To expand your knowledge further, check out resources like online tutorials, video courses, and documentation from reputable sources such as Cisco Networking Academy, Microsoft Learn, and Juniper Networks. Books like “Computer Networking: A Top-Down Approach” and “TCP/IP Illustrated, Volume 1: The Protocols” offer detailed explanations. Engage in networking forums, attend events, and connect with communities to learn from experts and like-minded individuals. Remember, continuous learning and staying updated are vital to mastering this dynamic field. So, embrace the world of networking and unleash its full potential!
For More amazing articles related to Tech Check out our website Over Here
To Read more similar articles click here
Thanks for visiting our Website. If you appreciate our work, kindly show us some support in our comments section 🙂